Access to the Systems
Accessing any section of the Cineca HPC systems requires activating two-factor authentication (2FA) for each user account. This enhanced security measure verifies a user’s identity by requiring a second, independent factor in addition to the account password. Even if the correct account password is used, 2FA ensures that unauthorized access is prevented, significantly improving the system’s overall security.
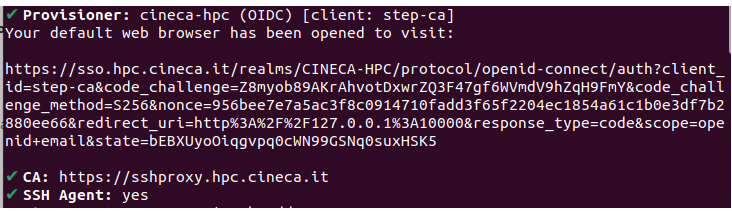
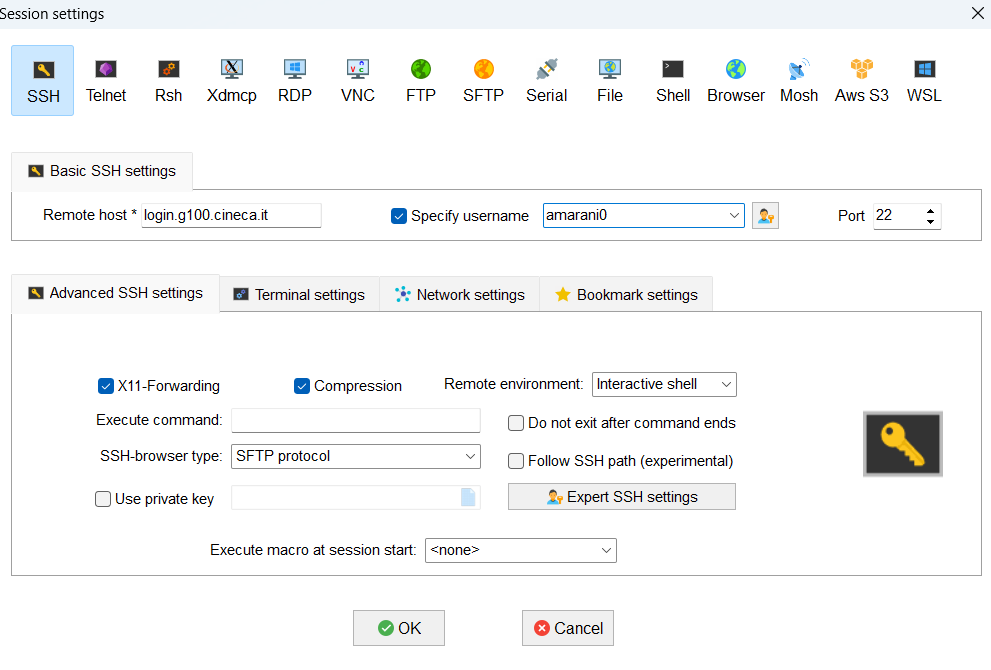
This access modality operates seamlessly for users, who continue to utilize standard protocols such as the SSH client. Before connecting to the cluster, users must request an SSH certificate from our Identity Provider (IP) via the smallstep client. Upon making the request, a web page will automatically open in the browser, prompting users to authenticate with our IP by entering a one-time password (OTP). Following successful authentication, the server will issue a time-limited certificate valid for 12 hours. This certificate allows users to connect to CINECA systems via SSH client.
Important
- For the First-time Access and the activation of 2FA, a user must complete the following steps:
Registration on UserDB.
Correct configuration of 2FA and OTP (How to activate the 2FA and the OTP generator).
Important
If you are a Cloud user only, smallstep installation is not required.
For HPC Resources you must use smallstep client to allow ssh protocol (How to configure smallstep client).
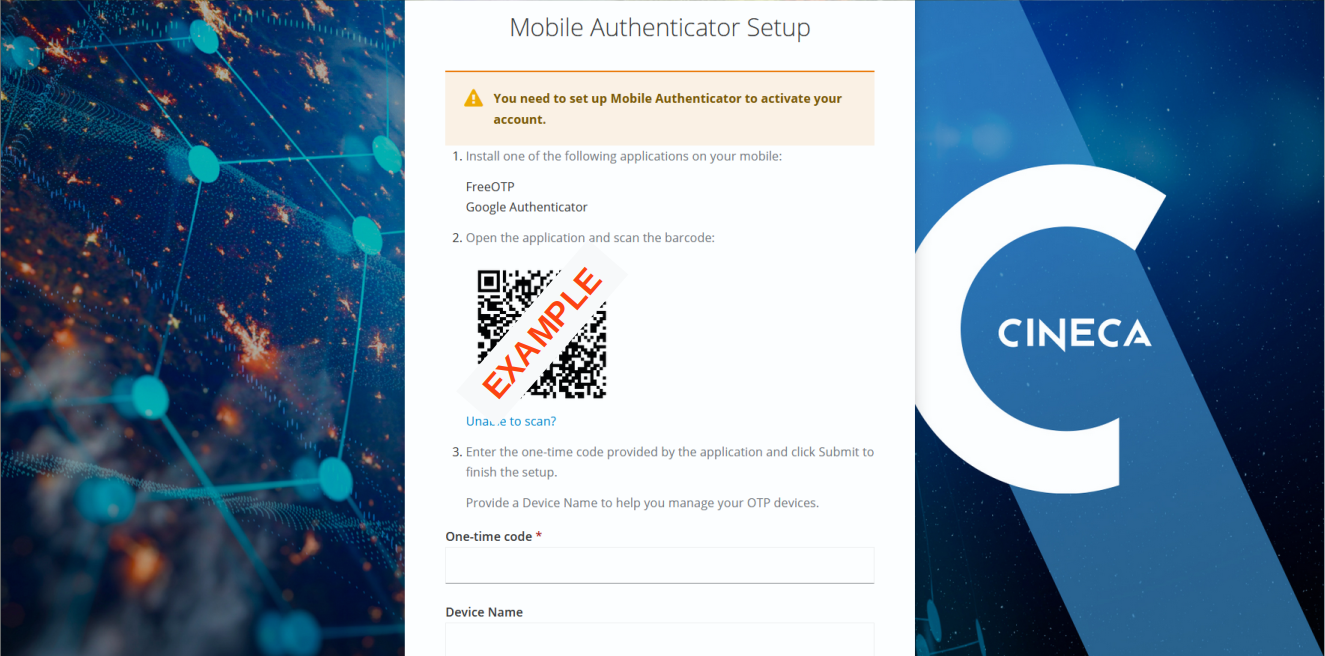
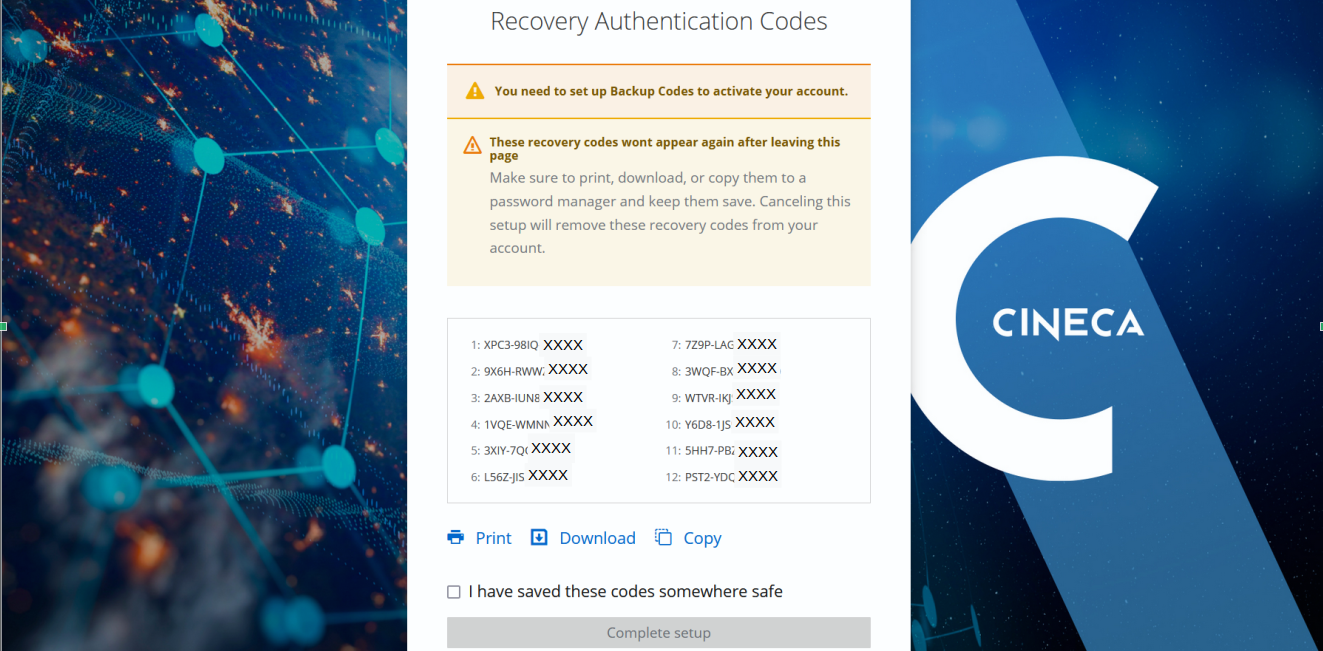
How to activate the 2FA and the OTP generator
Follow the instructions below to activate the 2FA authenticator method and configure the OTP generator.
Important
If you need to regenerate the OTP, please refer to the procedure outlined in the Manage your HPC credentials.
Users that want to get access only to Cloud resources can skip the next steps.
How to configure smallstep client
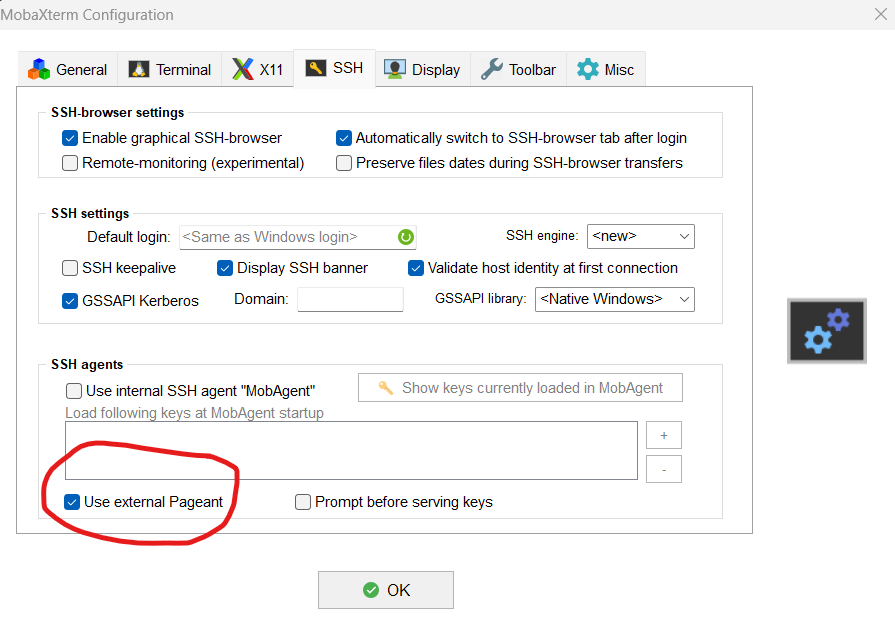
Once 2FA is enabled as authentication method for CINECA clusters, you will need to install and configure a 2FA-compatible program on your PC, to download the temporary certificate locally. At CINECA, we recommend using the Smallstep client.
Note
smallstep client is not required to access to cloud resources.
To obtain and install the Smallstep executable, visit the Smallstep website and follow the installation instructions for your operating system. Alternatively, you can download the executable directly from the GitHub repository.
After installation, you must configure Smallstep according to your operating system’s requirements. If you encounter any issues or need further assistance, please contact superc@cineca.it.
Windows users have multiple options:
How to manage authentication certificates
Managing authentication certificates in HPC environments involves ensuring secure access to resources. Users typically generate certificates via an Identity Provider or a local client, like Smallstep, for secure session authentication.
Key operations include:
Certificate generation: Performed during initial setup or when required by the system.
Re-generating certificates: Necessary if the current certificate expires or becomes invalid. Users typically log in to the portal or use a client tool to request a new certificate.
Certificate renewal: Ensures continued access without disruptions, often automated if supported by the system.
For issues or detailed procedures, users should consult the documentation or contact: superc@cineca.it.
Access via Secure Shell (SSH)
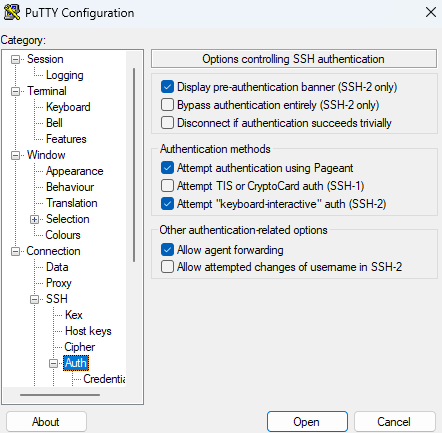
SSH is commonly employed for remote access to a machine, allowing users to execute commands (remote console), run programs, and transfer files securely. On Linux and Mac systems, the SSH client is typically pre-installed. However, on Windows systems, users need to download and install an SSH client. Some popular SSH clients for Windows include Powershell, openSSH, Putty or Tectia. Connection adopting 2FA procedure does not require to provide password.
The access is done via one of the following commands:
$ ssh <username>@login.marconi.cineca.it
$ ssh <username>@login.g100.cineca.it
$ ssh <username>@login.leonardo.cineca.it
$ ssh <username>@login.pitagora.cineca.it
You can use the option -X to enable X11 display forwarding.
Important
After 12 hours, a new certificate must be generated using the smallstep client (How to manage authentication certificates).
You will login to our systems with one of the two shells: bash or tcsh. Contact the HPC support (superc@cineca.it) if you want to change your default login shell.
Login is prevented on systems in which you don’t have a budget account.
We have identified a potential issue for local PC with openssh 8.6 (check with the command
ssh -V). The solution can be found here in our FAQ page.
Access via Remote Visualization (RCM)
Remote visualization has become popular as an HPC service since it allows to:
visualize the data produced on HPC infrastructure (scientific visualization)
analize and inspect data directy on the HPC infrastructure.
debug and optmization of codes via GUI tools directly on the HPC infrastructure.
All the aforementioned use cases can take advantage of use applications on the server side. The requirements to access to this service are the same for the access to HPC infrastructure. The remote visualization service at Cineca is provided through the Remote Connection Manager (RCM) application. Using this tool you can graphically inspect your data without moving them to your local work station.
Important
It can be used by any user with valid credentials to access CINECA clusters.
Continuous Integration (CI/CD) at CINECA
Continuous Integration, continuous delivery and deployment, also known as CI/CD, is the practice of a constant monitoring of the code development through the activation of an automatic pipeline. Every time a developer applies a change to the code, the automatic pipeline validates it by building the code and running some simple tests (typically unit tests).
CINECA has activated a new service where to run your Continuous Integration (CI/CD) pipelines on CINECA clusters, based on CINECA GitLab service. On Gitlab website there is a detailed documentation about CI/CD. This service is active on Galileo100, and is at the moment in an experimental phase.
Access via X.509 certificate
An X.509 certificate is issued by a trusted Certificate Authority (CA), which verifies the user’s identity and ensures the certificate is both valid and associated with a real individual. It is used as an authentication mechanism, serving as an alternative to traditional username/password credentials, and helps avoid the need to replicate user accounts across systems. When connecting to a service, the user’s certificate is mapped to a local account, under which all commands and operations are executed.
Important
Access to CINECA clusters no longer requires or supports X.509 certificates for authentication.
However, X.509 certificates may still be necessary for accessing certain external services or resources, such as data repositories, collaboration platforms, or grid computing infrastructures.
The following describes the procedure for obtaining an X.509 certificate and generating a proxy certificate for temporary use.
How to get your X.509 certificate
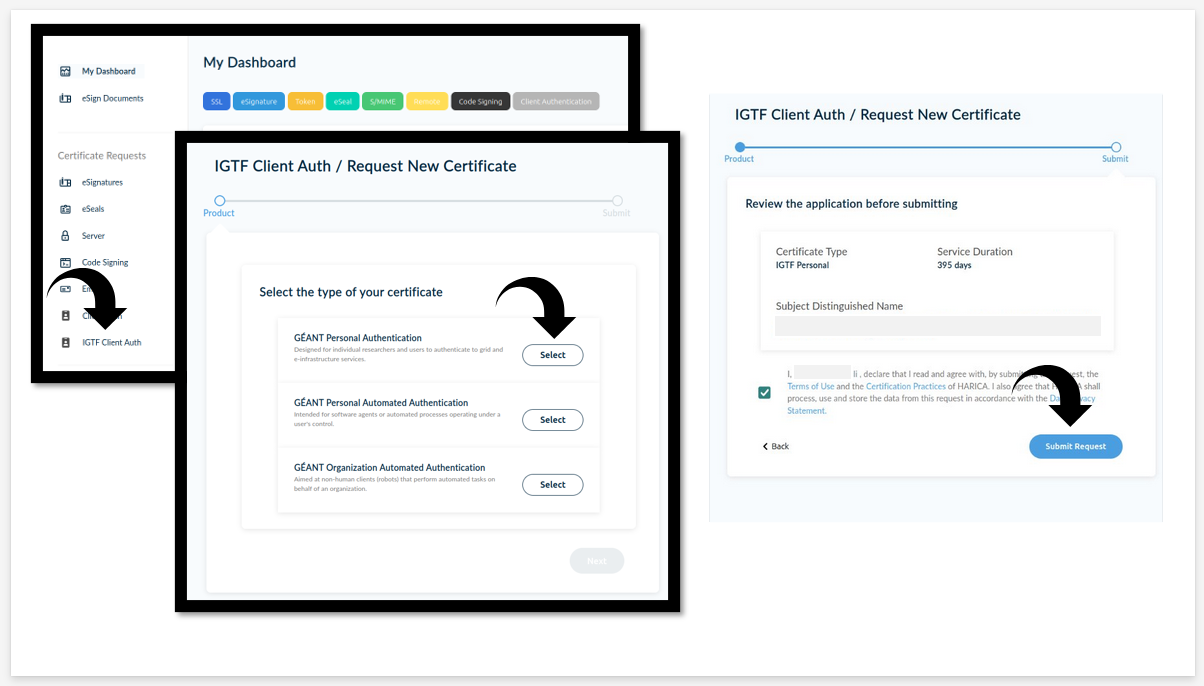
Users in need of an X.509 certificate can visit the HARICA website. Academic users can select Academic Login and authenticate using their institutional credentials.
In the dashboard’s left-hand menu, click on IGTF Certificate, then select GÉANT Personal Authentication.
Review and accept the terms and conditions, then click Submit Request.
Under Ready Certificates, click Enroll your Certificate. Choose your preferred algorithm (RSA or ECDF), then click Enroll Certificate again. After enrollment, click Download.
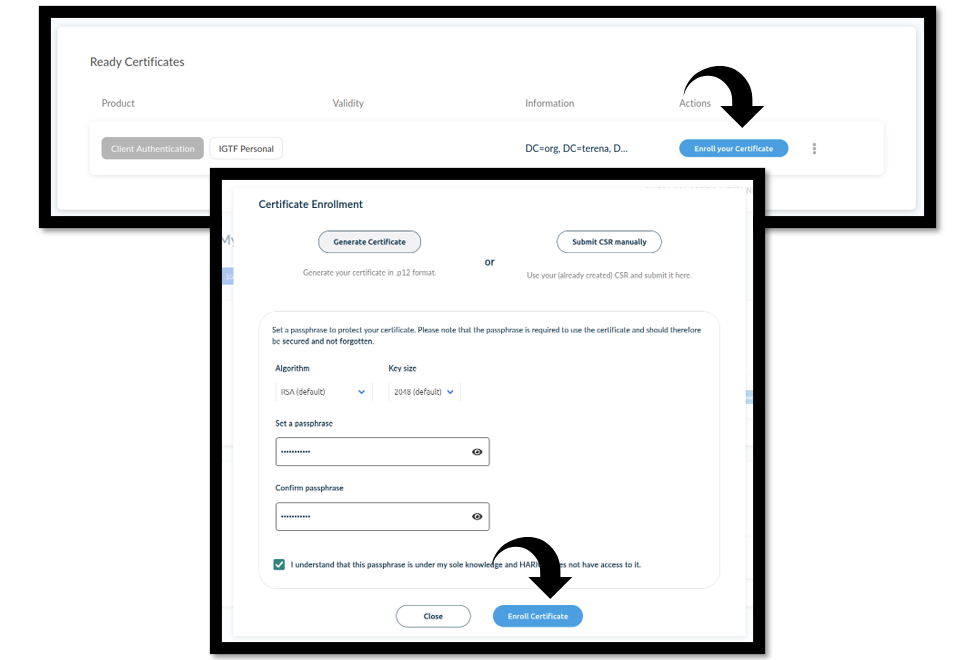
A
.p12file (containing your personal certificate and private key) will be downloaded.
How to Use Your X.509 Certificate (Browser and Command Line)
Once you have downloaded your .p12 certificate file, you can either:
Import it into your browser for web-based authentication.
Convert it into PEM format (
cert.pemandkey.pem) to use it with command-line tools such asgrid-proxy-init,voms-proxy-init, orglobus-url-copy.